Probable DPRK Nexus Actors Targeting Security Researchers
Yesterday, Google’s Threat Analysis Group (TAG) published a blog post identifying an ongoing campaign targeting security researchers working on vulnerability research and development. This activity was attributed to a North Korea nexus threat group. According to TAG, the threat group took its time building credibility with security researchers by creating a blog where the actors published analysis of publicly disclosed vulnerabilities. Further, the actors involved created multiple Twitter, Linkedin, Telegram, Discord, Keybase, and email accounts posing as security researchers. These accounts were used to tweet links to the blog, retweet accounts the threat actors controlled, and interact with the online information security community. This online activity resulted in the actors developing a list of targets and credibility building with the community, culminating in guest posts from legitimate security researchers on the threat actors’ blog.
Path to Compromise
The path to compromise for this campaign consisted of two methods. First, the threat actors tweeted links to a blog post which hosted a drive-by compromise infecting the target’s machine. To date, all of the compromised researchers were running up to date Windows 10 and Chrome browser versions, and the zero-day exploit used by the actors is not known at this time. Second, the actors capitalized on their built credibility by reaching out to researchers to ask if they would like to collaborate on vulnerability research. The targets were then given a Visual Studio Project, which included the exploit code for the vulnerability in question along with a malicious library functioning as a Command and Control (C2) beacon. Google is requesting any assistance in identifying the zero-day exploit used by the actors via its Vulnerability Reward Program.
Attribution
Attribution for this campaign was initially provided by Google, though we do not know what evidence drove this conclusion. However, Kaspersky’s Threat Attribution Engine has identified code similarities from the recent samples with the Manuscrypt malware family. Intezer Labs has published similar findings.
Manuscrypt has been distributed by the Lazarus Group since at least 2018, and has primarily been observed in campaigns targeting South Korean political targets as well as cryptocurrency exchanges. Last Spring, CISA released a Malware Analysis Report identifying samples associated with Lazarus Group activity, including the 2018 global data reconnaissance campaign attributed to the threat actor. Additionally, Lazarus Group has targeted researchers previously. In 2019, the threat actor targeted individuals associated with US-based think tanks and universities working on North Korea denuclearization research.
Conclusion
North Korean threat actors have become increasingly sophisticated over the last five years, and will likely be included in more organization’s threat models over the next five years. These threat actors have used cyber attacks — like the Sony Pictures attack and attack on South Korean ATMs — for coercive purposes and to steal from financial institutions and cryptocurrency exchanges. Recently, North Korean actors have been branching out into cyber-espionage to gain an understanding of their adversaries’ denuclearization assessments, to steal COVID-19 vaccine related information, and gain information about researchers working the North Korea target. Expect more activity from North Korea nexus actors if US-DPRK relations remain at an impasse.
IOCs
Actor controlled sites and accounts
Research Blog
Twitter Accounts
LinkedIn Accounts
https://www.linkedin.com/in/billy-brown-a6678b1b8/
https://www.linkedin.com/in/guo-zhang-b152721bb/
https://www.linkedin.com/in/hyungwoo-lee-6985501b9/
https://www.linkedin.com/in/linshuang-li-aa696391bb/
https://www.linkedin.com/in/rimmer-trajan-2806b21bb/
Keybase
Telegram
Sample Hashes
https://www.virustotal.com/gui/file/4c3499f3cc4a4fdc7e67417e055891c78540282dccc57e37a01167dfe351b244/detection (VS Project DLL)
https://www.virustotal.com/gui/file/68e6b9d71c727545095ea6376940027b61734af5c710b2985a628131e47c6af7/detection (VS Project DLL)
https://www.virustotal.com/gui/file/25d8ae4678c37251e7ffbaeddc252ae2530ef23f66e4c856d98ef60f399fa3dc/detection (VS Project Dropped DLL)
https://www.virustotal.com/gui/file/a75886b016d84c3eaacaf01a3c61e04953a7a3adf38acf77a4a2e3a8f544f855/detection (VS Project Dropped DLL)
https://www.virustotal.com/gui/file/a4fb20b15efd72f983f0fb3325c0352d8a266a69bb5f6ca2eba0556c3e00bd15/detection (Service DLL)
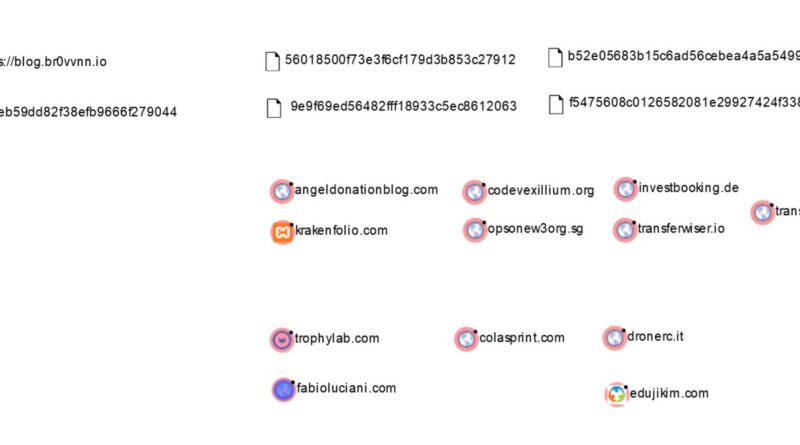
C2 Domains: Attacker-Owned
angeldonationblog[.]com
codevexillium[.]org
investbooking[.]de
krakenfolio[.]com
opsonew3org[.]sg
transferwiser[.]io
transplugin[.]io
C2 Domains: Legitimate but Compromised
trophylab[.]com
C2 URLs
https[:]//angeldonationblog[.]com/image/upload/upload.php
https[:]//codevexillium[.]org/image/download/download.asp
https[:]//investbooking[.]de/upload/upload.asp
https[:]//transplugin[.]io/upload/upload.asp
https[:]//www.dronerc[.]it/forum/uploads/index.php
https[:]//www.dronerc[.]it/shop_testbr/Core/upload.php
https[:]//www.dronerc[.]it/shop_testbr/upload/upload.php
https[:]//www.edujikim[.]com/intro/blue/insert.asp
https[:]//www.fabioluciani[.]com/es/include/include.asp
http[:]//trophylab[.]com/notice/images/renewal/upload.asp
http[:]//www.colasprint[.]com/_vti_log/upload.asp
Host IOCs
Registry Keys
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\KernelConfig
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DriverConfig
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SSL Update
File Paths
C:\Windows\System32\Nwsapagent.sys
C:\Windows\System32\helpsvc.sys
C:\ProgramData\USOShared\uso.bin
C:\ProgramData\VMware\vmnat-update.bin
C:\ProgramData\VirtualBox\update.bin